Non-Human Identities (NHI) – Cybersecurity Challenges and Solutions
Introduction
The landscape of identity management in modern IT environments has evolved significantly, extending beyond human users to include Non-Human Identities (NHI). These identities encompass service accounts, application accounts, machine identities, bots, and IoT devices, which are instrumental in automation, system integrations, and enhancing operational efficiencies. However, the governance and security of these identities pose distinct challenges. If not effectively managed, NHIs can become major vulnerabilities within an organization’s cybersecurity framework, leading to unauthorized access, data breaches, and system compromises.
Understanding Non-Human Identities (NHI)
Non-Human Identities refer to digital identities assigned to applications, services, or devices rather than individual users. These identities serve as authentication and authorization mechanisms, granting access to essential resources such as databases, cloud services, and internal systems to facilitate seamless automation and application functionality. Key types of NHIs include:
Service Accounts – These accounts are used to run background processes, applications, and scheduled system tasks without requiring human intervention.
API Keys & Tokens – Secure authentication mechanisms that enable communication between different applications and services.
Robotic Process Automation (RPA) Bots – Automated software bots designed to perform repetitive business and IT tasks, often requiring elevated privileges.
Cloud Workloads – Includes virtual machines, containers, and serverless functions that interact within cloud environments and often require identity-based authentication.
IoT Devices – Internet-connected smart devices that transmit data, interact with enterprise systems, and often operate autonomously.
Due to the absence of human oversight, traditional identity governance strategies that focus on manual interventions are often ineffective for NHIs. This can lead to security loopholes, making it imperative to establish robust mechanisms for monitoring and securing these identities.
Cybersecurity Challenges with NHIs
1. Lack of Visibility and Inventory Management
One of the most significant challenges organizations face is the inability to maintain a comprehensive and updated inventory of NHIs. Without centralized visibility, it becomes difficult to track existing accounts, their ownership, their purpose, and their access privileges. This lack of oversight contributes to security blind spots and increases the likelihood of shadow IT, where unauthorized NHIs operate without proper security controls.
2. Weak or Hardcoded Credentials
Many NHIs rely on passwords, API keys, or certificates that are often embedded within application source code, scripts, or configuration files. This practice, known as hardcoded credentials, creates a significant security risk. If these credentials are exposed—whether through misconfigurations, repository leaks, or insider threats—attackers can exploit them to gain unauthorized access to critical systems.
3. Overprivileged Access
A common security issue with NHIs is that they are granted excessive permissions, sometimes due to a lack of granular access controls or poor administrative practices. Overprivileged NHIs pose a serious threat because if an attacker gains access to a compromised identity, they can move laterally within an organization’s network, escalating privileges and accessing sensitive resources.
4. Inadequate Lifecycle Management
Unlike human identities, NHIs do not have clear lifecycle management processes in place. This means that service accounts and associated credentials often persist long after an application has been decommissioned. These orphaned NHIs remain active indefinitely, providing a potential attack vector for malicious actors.
5. Lack of Multi-Factor Authentication (MFA) for NHIs
While MFA is a standard security measure for human identities, its implementation for NHIs remains limited. Without strong authentication mechanisms, NHIs become susceptible to brute-force attacks, credential stuffing, and unauthorized access attempts.
6. Insufficient Monitoring and Auditing
Security monitoring solutions are often designed to detect suspicious activity associated with human users, but they may lack the capabilities to track anomalies in machine-to-machine interactions. As a result, a compromised NHI can remain undetected for extended periods, allowing attackers to exfiltrate data, execute malicious commands, or compromise system integrity without raising immediate alarms.
Real-World Examples of NHI Security Breaches
Capital One Data Breach (2019): Misconfigured AWS IAM roles allowed an attacker to exploit an overprivileged service account, resulting in the exposure of 106 million records.
Tesla Kubernetes Attack (2018): Hackers exploited an exposed Kubernetes admin console with weak credentials, hijacking Tesla’s cloud resources for cryptomining.
Code Spaces Breach (2014): Attackers gained unauthorized access to an AWS account using a compromised API key, leading to the company's permanent shutdown.
Solutions for Securing Non-Human Identities
1. Implement a Centralized Identity Inventory
To ensure effective governance, organizations should maintain an up-to-date repository of all NHIs, detailing their purpose, ownership, and levels of access. Implementing solutions such as Identity Governance and Administration (IGA) and Privileged Access Management (PAM) helps create a structured framework for managing NHIs across their lifecycle.
2. Enforce Strong Credential Management
Utilize vaulting solutions such as CyberArk, HashiCorp Vault, or AWS Secrets Manager to store API keys, secrets, and passwords securely.
Automate credential rotation to prevent long-lived credentials that could be exploited if compromised.
Eliminate hardcoded secrets by replacing them with secure vault integrations or dynamically injected credentials through environment variables.
3. Apply Least Privilege Access Controls
Implement role-based access control (RBAC) and attribute-based access control (ABAC) to assign the minimum required privileges for each NHI.
Leverage Just-in-Time (JIT) access provisioning to provide temporary, time-bound permissions instead of static access rights.
Conduct periodic access reviews to revoke unnecessary privileges and ensure that NHIs operate under the principle of least privilege.
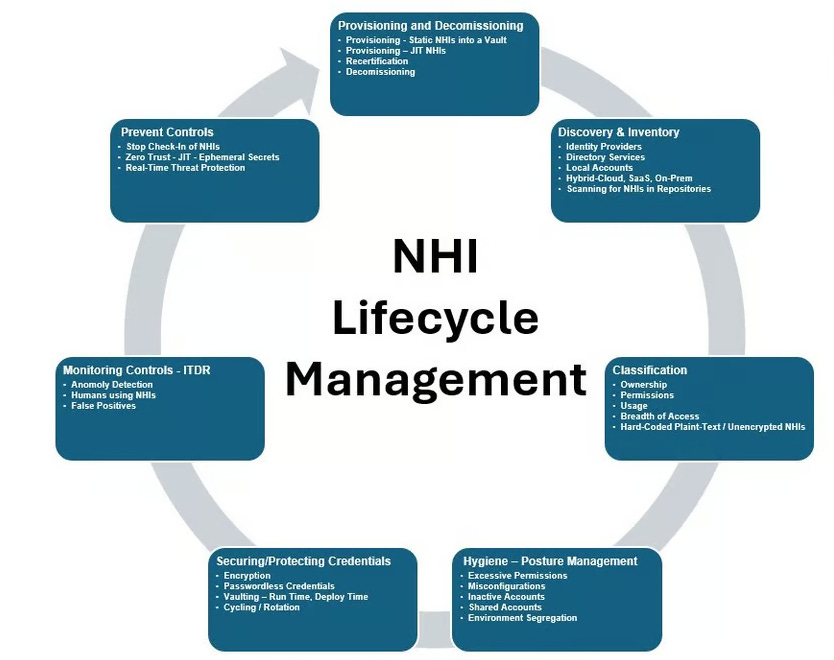
Image source: The Ultimate Guide To Non-Human Identities by Lalit Choda, NHI Mgmt Group
Best Practices: Essential Guidelines for Securing NHIs
Recommended Practices (Dos):
✔ Maintain a Comprehensive Inventory – Establish and continuously update a centralized repository of all NHIs, detailing their ownership, access privileges, and associated risks.
✔ Enforce Stringent Credential Hygiene – Implement robust password policies, eliminate hardcoded secrets, and leverage secure storage solutions such as secret vaults.
✔ Leverage IAM Solutions for Access Governance – Utilize Identity and Access Management (IAM) solutions to enforce policy-driven controls, ensuring that NHIs operate within defined security parameters.
✔ Conduct Regular Audits and Credential Rotation – Periodically review and update NHI credentials to mitigate risks associated with long-lived access tokens and stale permissions.
✔ Implement Continuous Monitoring and Anomaly Detection – Deploy real-time monitoring solutions to detect and respond to unusual NHI behaviors, mitigating the risk of unauthorized access or privilege abuse.
Prohibited Practices (Don’ts):
✖ Avoid Assigning Excessive Permissions – Grant NHIs only the minimum privileges required for their intended function, adhering to the principle of least privilege (PoLP).
✖ Never Store Credentials in Source Code or Plaintext – Ensure all authentication secrets are securely managed within vaulting solutions rather than being embedded in code repositories.
✖ Do Not Use Static Credentials with Extended Lifespans – Replace persistent credentials with short-lived, dynamically generated tokens to reduce exposure risk.
✖ Do Not Overlook Orphaned NHIs – Decommission NHIs promptly when they are no longer in use to prevent unauthorized access and security vulnerabilities.
✖ Refrain from Treating NHIs as Secondary to Human Identities – Ensure NHIs receive the same level of security oversight as human identities, recognizing their critical role in system automation and operational workflows.
Conclusion
As organizations accelerate their adoption of automation, cloud computing, and AI-driven technologies, securing Non-Human Identities (NHI) is no longer optional but a necessity. Poorly managed NHIs create significant security risks, including credential leaks, privilege escalation, and system vulnerabilities, potentially leading to devastating breaches. To counter these threats, organizations must integrate comprehensive identity governance frameworks, enforce least privilege access controls, and implement continuous monitoring for anomaly detection. The same level of security diligence applied to human identities must be extended to NHIs, ensuring compliance with regulatory standards and reinforcing trust in an increasingly interconnected digital landscape. By proactively adopting best practices, leveraging advanced IAM solutions, and fostering a security-first culture, organizations can safeguard their digital assets, minimize attack surfaces, and build a resilient cybersecurity posture that is prepared for future challenges.
Some Reference articles :-
"Best Practices For Mitigating Non-Human Identity Risk" – This Forbes article outlines strategies for identifying and managing NHIs to reduce security vulnerabilities. Forbes
"Seven Best Practices for Managing Non-Human Identities" – Published by SC Media, this piece provides a comprehensive guide on effective NHI management techniques. SC Media
"How To Manage and Secure Non-Human Identities" – LBMC discusses the importance of NHIs and offers practical steps for their secure management. LBMC
"What Are Non-Human Identities, Their Challenges and Solutions?" – This article delves into the complexities of NHIs and proposes solutions to common challenges.
"What is a Non-Human Identity?" – CyberArk provides an overview of NHIs, associated challenges, and best practices for their management. CyberArk
About the Author
Sameer Bhanushali is a seasoned IT professional with extensive experience in designing and implementing robust security frameworks. Sameer has been instrumental in advancing security practices across various sectors. He holds advanced certifications in IAM and Security.
As an Architect, Sameer specializes in helping organizations navigate the complexities of modern cybersecurity challenges, focusing on enhancing security posture through innovative solutions and best practices. His commitment to advancing the field of cybersecurity is reflected in his thought leadership and dedication to protecting sensitive information in an ever-evolving threat landscape.