🔐 Evolving Security with Precision: New Advancements in Azure Conditional Access
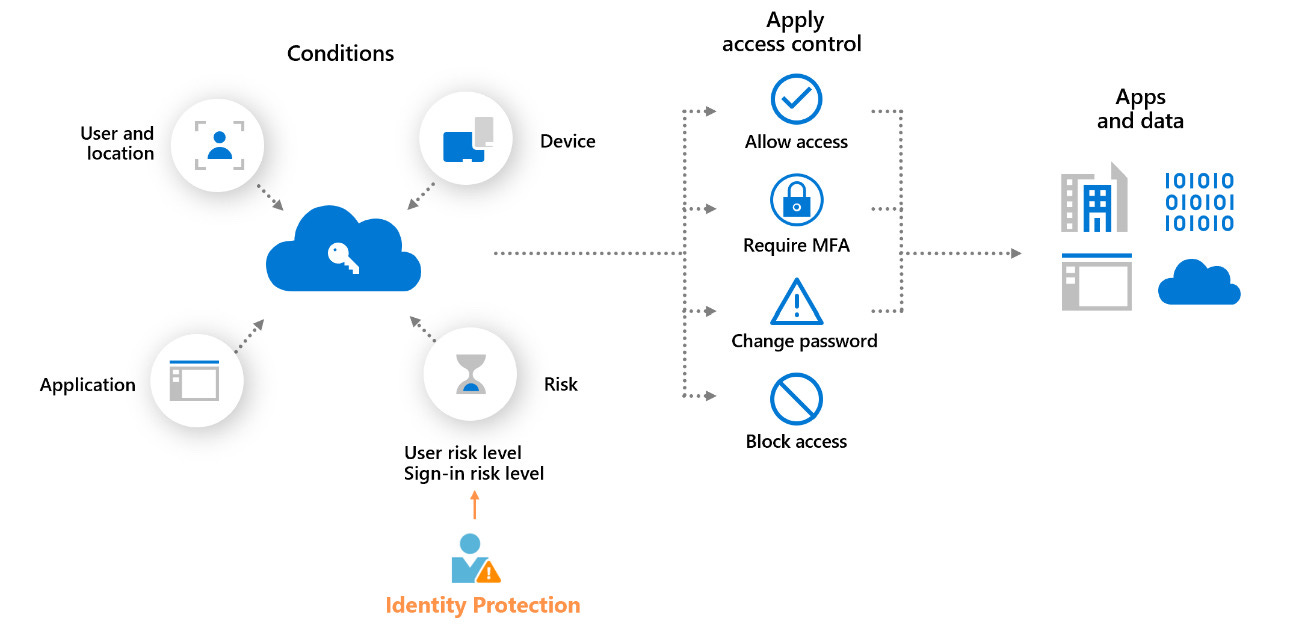
In the modern digital enterprise, identity has become the new security perimeter. As organizations continue their journey toward a Zero Trust architecture, Microsoft Entra ID (formerly Azure Active Directory) has established itself as the backbone of identity-centric security. At the core of this strategy lies Conditional Access — a powerful policy engine that enforces access decisions based on contextual signals, user risk, and compliance requirements.
Microsoft has recently introduced several enhancements to Conditional Access that significantly strengthen its capabilities. These new features are designed to provide administrators with greater granularity, adaptability, and intelligence, ensuring secure access without disrupting productivity
🚀 Key Enhancements in Conditional Access
1️⃣ Authentication Strengths
Previously, Conditional Access policies could enforce MFA, but lacked control over which method was used. With Authentication Strengths, administrators can now mandate specific authentication methods such as:
Phishing-resistant MFA (FIDO2 security keys, Windows Hello for Business, certificate-based authentication)
Compliant mobile app-based MFA for medium-risk scenarios
Use Case: An organization may enforce FIDO2 keys for financial systems while permitting push notifications for internal collaboration tools.
Benefit: This closes the gap where attackers exploit weaker MFA methods (e.g., SMS OTPs) and ensures high-value resources are protected with the strongest factors.
2️⃣ Granular Session Controls
Conditional Access now extends beyond authentication, applying controls within user sessions. Through integration with Microsoft Defender for Cloud Apps (MDCA), administrators can:
Restrict downloads or printing from SharePoint Online when a device is unmanaged
Block file uploads to third-party applications if a session risk is detected
Apply continuous monitoring to sensitive sessions
Benefit: Protects sensitive data even after successful authentication, ensuring post-login visibility and control.
3️⃣ Continuous Access Evaluation (CAE)
Traditional session tokens are valid until expiration, leaving potential exposure windows. With CAE, access is revalidated in near real time when conditions change, such as:
User’s account risk level increases
Password is reset
User signs out from another session
User’s location changes unexpectedly
Use Case: If a privileged account logs in from the U.S. and shortly after an attempt is made from overseas, CAE forces re-authentication immediately.
Benefit: Minimizes exposure time and strengthens session security.
4️⃣ Enhanced Named Locations & IP Intelligence
Conditional Access policies can now incorporate advanced IP intelligence and location context:
Blocking traffic from anonymous IP addresses, TOR exit nodes, or known malicious IP ranges
Defining trusted corporate networks with greater accuracy
Applying dynamic risk-based location conditions
Benefit: Adds context-aware defenses against attackers who leverage VPNs, proxies, or malicious infrastructure.
5️⃣ Custom Authentication Contexts
This enhancement allows policies to enforce step-up authentication at the transaction level. Instead of requiring strong MFA across an entire application, organizations can secure only sensitive workflows.
Example:
Accessing the HR portal may only require standard login
Downloading confidential payroll records may require a phishing-resistant authentication method
Benefit: Provides granular, risk-aligned access controls that balance security with user experience.
6️⃣ Policy Templates, Insights, and Recommendations
To simplify deployment, Microsoft has introduced ready-to-use policy templates, such as:
Blocking legacy authentication
Securing privileged admin accounts
Enforcing MFA for external collaborators
In addition, policy insights highlight gaps, misconfigurations, and policy overlaps.
Benefit: Helps organizations adopt best practices quickly and ensures a stronger, consistent security baseline.
🌐 Strategic Implications for Enterprises
Improved Threat Resilience: Stronger MFA enforcement and real-time session re-evaluation protect against token theft, MFA fatigue attacks, and session hijacking.
Regulatory Alignment: Many compliance frameworks (NIST, PCI DSS, HIPAA) now emphasize phishing-resistant authentication — features like Authentication Strengths directly address these requirements.
Operational Efficiency: Templates and insights reduce administrative overhead and speed up policy adoption.
Enhanced User Experience: By applying friction only when necessary, Conditional Access maintains productivity while adapting to context and risk.
💡 Conclusion
The latest advancements in Microsoft Entra Conditional Access reflect Microsoft’s commitment to enabling a dynamic, identity-driven defense strategy. No longer limited to “allow” or “block,” Conditional Access has matured into a contextual, adaptive policy framework that continuously evaluates risk signals and enforces controls in real time.
For organizations adopting or strengthening their Zero Trust journey, leveraging these new Conditional Access capabilities is no longer optional — it is essential. By embracing these features, security leaders can ensure resilient protection of identities, data, and applications, while delivering a seamless user experience across hybrid and cloud environments.
Reference
About the Author
Sameer Bhanushali is a seasoned IT professional with extensive experience in designing and implementing robust security frameworks. Sameer has been instrumental in advancing security practices across various sectors. He holds advanced certifications in IAM and Security.
As an Architect, Sameer specializes in helping organizations navigate the complexities of modern cybersecurity challenges, focusing on enhancing security posture through innovative solutions and best practices. His commitment to advancing the field of cybersecurity is reflected in his thought leadership and dedication to protecting sensitive information in an ever-evolving threat landscape. 🔗 LinkedIn Profile
Thanks for reading TechSecure Insights!This post is public so feel free to share it.
Thanks for reading TechSecure Insights! Subscribe for free to receive new posts and support my work.